
Clave Wallet
www.getclave.ioStats
Daily Transaction Count
Daily Deployed Clave Account
Daily Active Account Count
Weekly Active Account Count
Activity
Clave Contracts
0 contributors in the last year
Clave Expo Passkey
0 contributors in the last year
Clave Lists
0 contributors in the last year
Security Analysis
Key Management
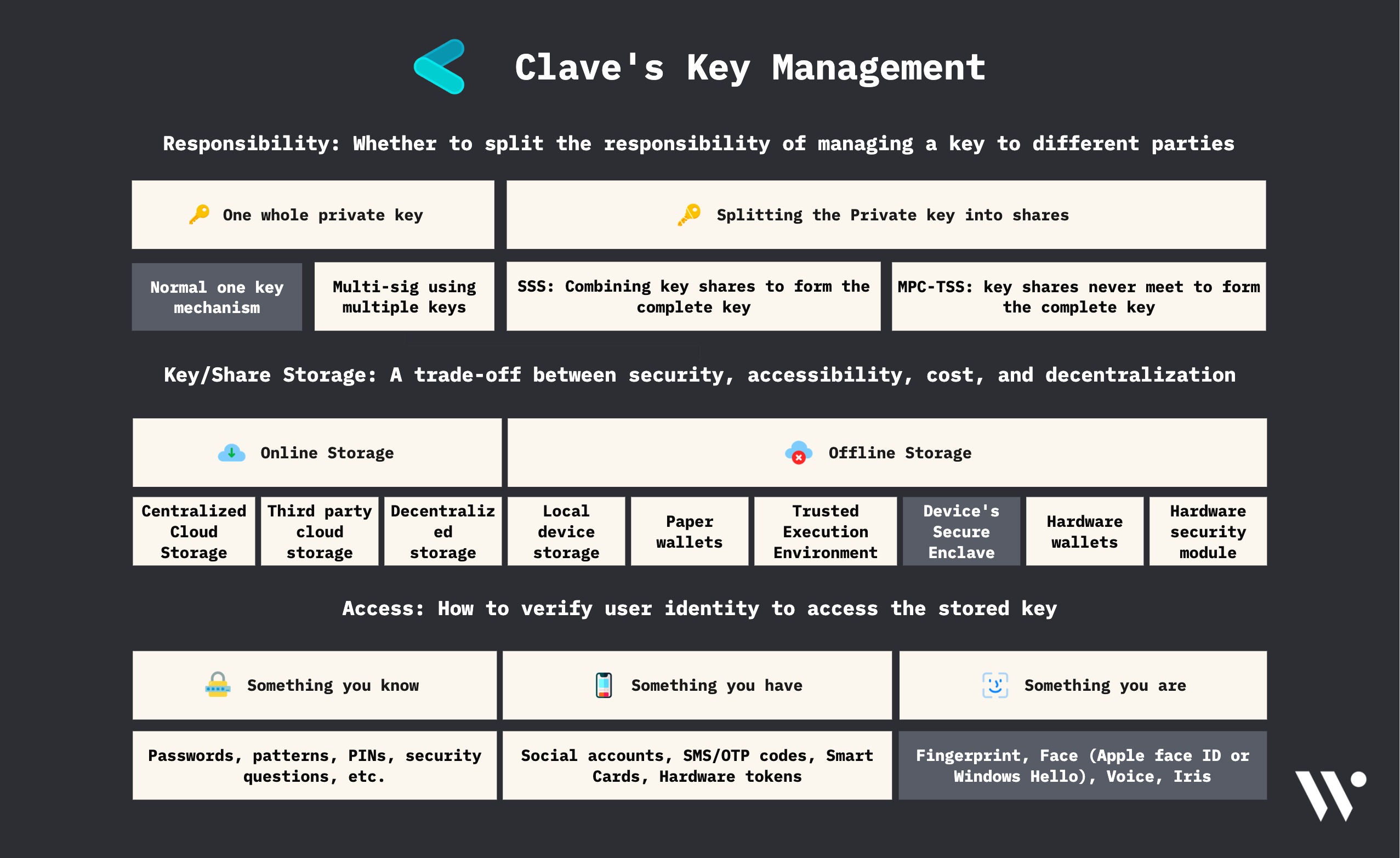
Responsibility
A single user is responsible for managing the private key (secp256r1passkey in this case).
Storage
The passkey is generated by the device’s Secure Enclave (in case of iOS devices) or similar modules (in case of Android devices). The passkey is locally stored on the device’s Secure Enclave (in case of iOS devices) or similar modules (in case of Android devices).
Access
The user can access Secure Enclave (in case of iOS devices) or similar modules (in case of Android devices) in order to perform different operations without the passkey ever leaving the Secure Enclave.
Account Management
Clave does not support Externally Owned Accounts (EOAs) but it does support Smart Contract Accounts (SCAs).
Clave’s SCA Implementation
Clave maintains their own SCA implementation.
Registry
Clave maintains their own and ModuleManager and HookManager.
Modules
Clave also has 2 module implementations: SocialRecoveryModule and CloudRecoveryModule.
- SocialRecoveryModule: The Social recovery module allows clave users to assign guardians to their account who can help recovery your wallet.1struct RecoveryConfig {2uint128 timelock; // Recovery timelock duration3uint128 threshold; // Recovery threshold4address[] guardians; // Guardian addresses5}
Each account has a
RecoveryConfigwhich defines:timelockdefines the duration of the recovery period (see recovery section for more context).thresholddefines the minimum number of guardians that need to approve the recovery of an account. Note that thethresholdwill always be less than or equal to the number ofguardiansassociated with the account.guardiansis an array of guardian addresses associated with an account.
We’ll discuss how this module is used for recovery in this section.
- CloudRecoveryModule: The cloud recovery module recovers an account using a key stored in iCloud or other similar clouds. This module is no longer used in the current Clave app because passkeys can sync with different user devices.
Processes
Clave has the following processes in place:
Key Generation
- User (mobile wallet) receives a challenge string the Clave server. This challenge string is then used as an input (
bytes32 salt) to generate the (counterfactual) account address (using the getAddressForSalt function). A counterfactual account address means that the actual smart contract account is not deployed on the address yet, but if we use the same salt (challenge string) to deploy a smart contract account (using the deployAccount function), it’ll be deployed to the same address that was generated by the getAddressForSalt function. Once the user has the counterfactual account address, we’ll generate a key pair. In order to do so, we’ll first need to create a
publicKeyCredentialCreationOptionsobject.Here is an example (actual implementation might differ) of how the
publicKeyCredentialCreationOptionsobject looks like:challengeparameter is generated using the challenge string that we got from the Clave server (which israndomStringFromServerin the code snippet). This is used to prevent “replay attacks” (more info here).rpwhich is also known as the relaying party basically defines the describing the organization responsible for registering and authenticating the user. In this case, it’s Clave! (more info here).userdefines the user currently registering. The counterfactual account address is used as theidparameter. It is suggested to not use personally identifying information as theid, as it may be stored in an authenticator. Read the spec (more info here).pubKeyCredParamsdescribes what public key types (in this case,secp256r1) are acceptable to a server (Clave).
Rest of the params are optionally filled and are same for every user.
1const publicKeyCredentialCreationOptions = {2challenge: Uint8Array.from(3randomStringFromServer, c => c.charCodeAt(0)),4rp: {5name: "Clave wallet",6id: "getclave.io",7},8user: {9id: Uint8Array.from(10"UZSL85T9AFC", c => c.charCodeAt(0)),11name: "vasa.develop@gmail.com",12displayName: "vasa",13},14pubKeyCredParams: [{alg: -7, type: "public-key"}],15authenticatorSelection: {16authenticatorAttachment: "cross-platform",17},18timeout: 60000,19attestation: "direct"20};Once we have the
publicKeyCredentialCreationOptions, we use the register function to get aPasskeyRegistrationResultobject. ThisPasskeyRegistrationResultobject is then sent to the clave server to be parsed and validated. Note that under the hood, the register function generates a key pair; the private key is stored in the secure enclave and never leaves the enclave, whereas the public key can be shared publicly.1import { Passkey, PasskeyRegistrationResult } from 'react-native-passkey';23// Retrieve a valid FIDO2 attestation request from your server4// The challenge inside the request needs to be a base64 encoded string5// There are plenty of libraries which can be used for this (e.g. fido2-lib)67try {8// Call the `register` method with the retrieved request in JSON format9// A native overlay will be displayed10const result: PasskeyRegistrationResult = await Passkey.register(requestJson);1112// The `register` method returns a FIDO2 attestation result13// Pass it to your server for verification1415console.log(result);1617// PasskeyRegistrationResult {18// id: 'ADSUllKQmbqdGtpu4sjseh4cg2TxSvrbcHDTBsv4NSSX9...',19// rawId: ArrayBuffer(59),20// response: AuthenticatorAttestationResponse {21// clientDataJSON: ArrayBuffer(121),22// attestationObject: ArrayBuffer(306),23// },24// type: 'public-key'25// }26} catch (error) {27// Handle Error...28}
Account Generation/Activation
If everything goes well in step 3, Clave will deploy the smart contract wallet (using the deployAccount function) whenever the user performs their 1st trx from the clave wallet (here is an example transaction ). As we discussed in step 1, the smart contract wallet will be deployed at the counterfactual account address as we will use the same salt to deploy the account that was used to pre generate the address.
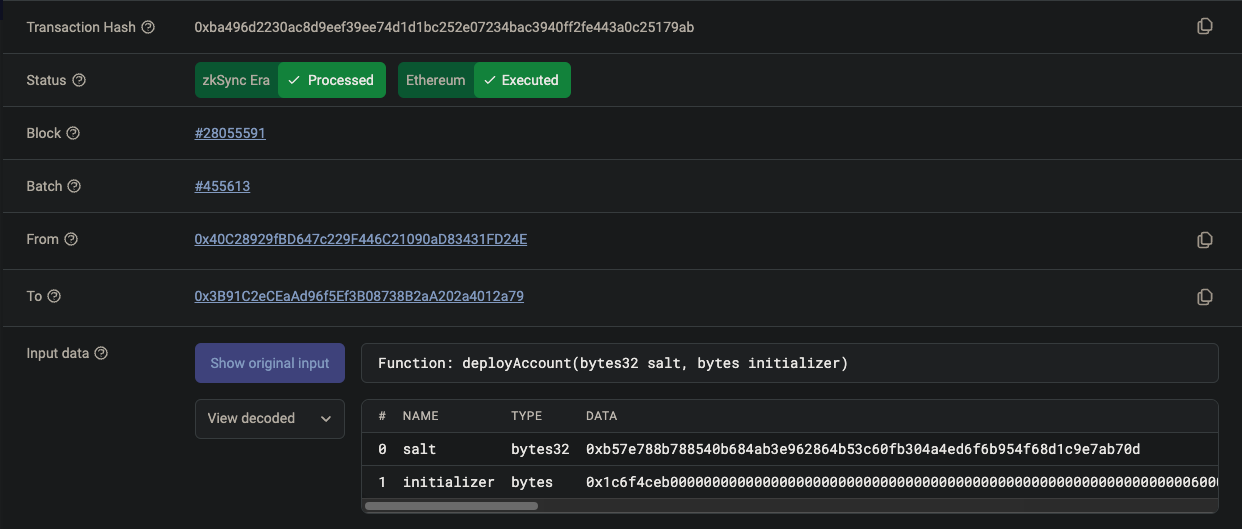
An example transaction showing how Clave wallet deploys user’s SCA on the first transaction from the Clave wallet (trx link) The public key (hex encoded version of
idfromPasskeyRegistrationResult) will also be passed (within theinitializerparameter) which will set it as the owner of the SCA.
Transaction Process
Key signing : The app takes a transaction message and forwards a signing request to the Secure Enclave. The user can then use biometric authentication to approve signing after which the Secure Enclave signs the message with the key.
Transaction verification : The signed message from the Secure Enclave is then relayed to the bundler (which is also the sequencer in case of zksync due to native AA support) which sends the transaction to the SCA which uses a verifier contract to validate the secp256r1 signature. Note that in April of 2024, zksync will add native support for EIP-7212, and Clave can then use the native circuit implementation to verify secp256r1 signatures in a much cheaper way.
Gas abstraction/sponsership : Clave wallet sponsors first few (~5) transactions using a paymaster.
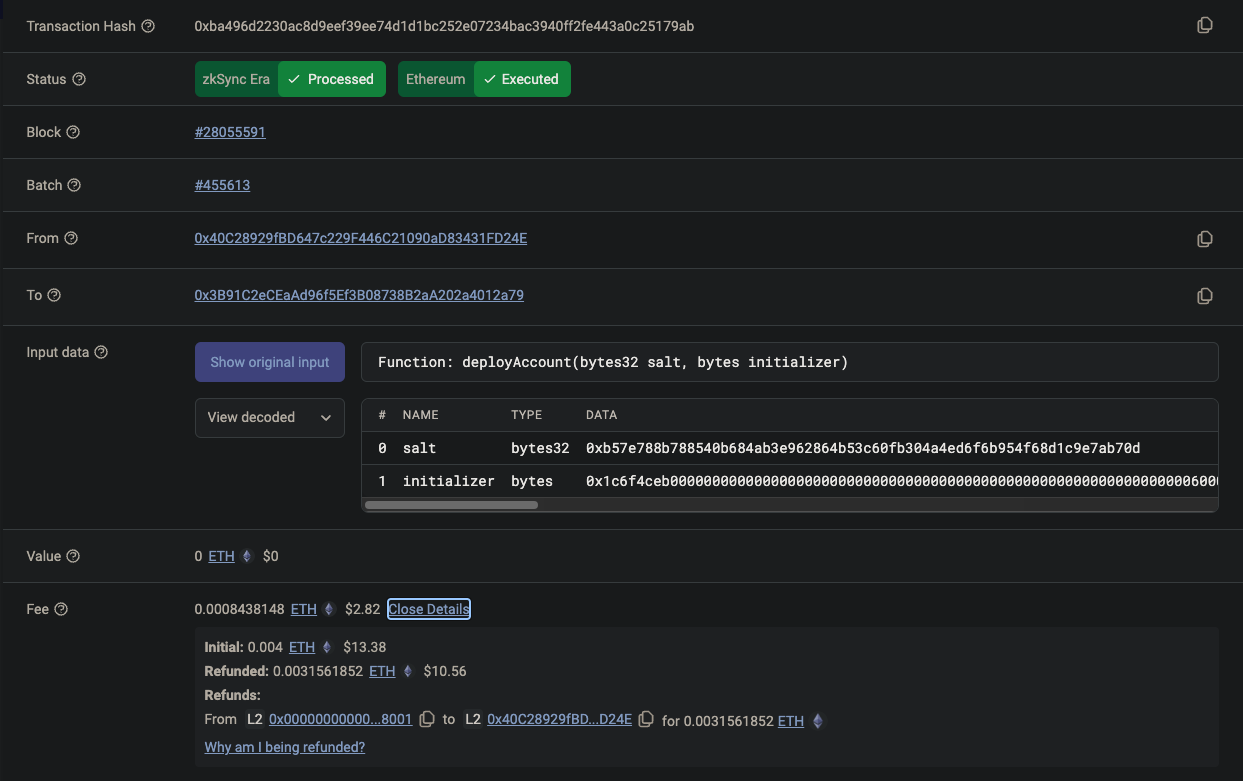
An example transaction showing the fee paid by the paymaster.
Account Recovery Process
Clave wallet supports social recovery mechanism where the user can assign their family or friend’s clave address as backup guardians. Users can decide the number of guardians that have to give confirmation for recovery (M our of N guardians where N ≥ M).
The recovery process is conducted by Clave’s smart contract on zkSync. Once the user initiates the recovery flow:
- The user is asked to share the address (or nick name that Clave uses as a temporary solution before ENS is added to zksync) that needs to be recovered.
- Next, the user is asked the address (or nick name) of their guardian. Note that while Clave’s social recovery module does support recovery using M out of N guardians, but the app currently only works for recovery using a single guardian (i.e. for all users, the threshold is set to 1).
- Next, a new passkey is generated (using the process discussed here ). Your device might ask for a biometric authentication to save the newly generated passkey to the cloud (for eg. in case of iOS, it will be stored on the iCloud keychain).
- The app will then share a link that the user can share with your guardian. This link contains the details needed by the guardian to generate a signature to initiate the recovery process for the user.
- Once the guardian uses the link, they will be prompted to sign a message that signifies their consent to recover the user’s account.
- Next, the guardian will sign a transaction that calls the
startRecoveryfunction which which will validate the signature from the previous step and start a 48-hour time lock. - Once the 48-hour duration is complete, anyone can call the
executeRecoveryfunction that will update the owner of the SCA with the new public key that we created in step 3.
Note that the user can chose to cancel the recovery process (using the startRecovery function) anytime within the 48 hours time lock period. This feature is useful in case the user initiated the recovery process by mistake or to prevent any unauthorized and malicious activities.
Migrating from another wallet (assuming migration on a single network; zksync)
Case 1: If you are migrating from an EOA account: You would need to transfer all your assets from your EOA to the Clave account contract. In future this can be made easier with (EIP-7377 migration transaction).
Case 2: If you are migrating from a smart contract account: You would need to transfer all your assets from your smart contract account to the Clave account contract. Ideally, this could be done in a single transaction given we can batch transactions with a smart contract account.
Migrating to another wallet (assuming migration on a single network)
You should be able to transfer all your assets to any other address in a single transaction.
What happens to the wallet if clave servers/platform is down?
TODO
Features
In App
Security
ENS Support
Hardware Wallet Supports
Supported Standards
Incentives
No incentives
Security
Audit
Audits in Web3 refer to the process of conducting comprehensive security assessments and evaluations of blockchain-based projects, smart contracts, decentralized applications (dApps), and other Web3 protocols. The purpose of these audits is to identify vulnerabilities, potential risks, and weaknesses in the code and system architecture to enhance security, reliability, and trustworthiness.
Bug Bounty
A bug bounty program in Web3 is an initiative offered by blockchain projects, cryptocurrency platforms, or decentralized applications (dApps) to incentivize security researchers and ethical hackers to discover and report vulnerabilities or bugs in their systems. It is a crowdsourced approach to security testing where individuals or teams are rewarded for responsibly disclosing vulnerabilities they find.
Past Incidents
Legal Compliance
Legal Compliance refers to the wallet's adherence to relevant laws, regulations, and guidelines in the jurisdictions in which it operates. This includes regulations regarding user data privacy, anti-money laundering (AML), Know Your Customer (KYC) processes, and more. Compliance ensures that the wallet operates in a legal and ethical manner, providing users with a secure and trustworthy platform for managing their digital assets.
Where is the company registered?
This is important as it can impact the regulatory standards the company must adhere to, the legal protections available to users, and the company's overall credibility and trustworthiness.
London, United Kingdom
Data Safety Policy
It's essential for ensuring the privacy and security of user data, demonstrating the company's commitment to maintaining user trust and adhering to data protection regulations. It provides users with an understanding of what to expect regarding their personal information when using the wallet.
https://www.getclave.io/privacy-policy
Website Cookie policy
Website cookies in this wallet are used for:
https://www.getclave.io/privacy-policy